工作中需要检测服务所用的TLS套件版本等,可以用以下几种工具
1 工具汇总
ssllabs
强烈推荐这个网站,简洁直观,非常好
https://www.ssllabs.com/
htbridge
这个网站检测全面,SSL检测项目更新最快
https://www.htbridge.com/ssl/
myssl
这个网站是中国特供,国内访问速度最快,并提供对各大国产浏览器的SSL检测
https://myssl.com
testssl
非常全的工具 https://testssl.sh/
2 sslscan
- 是否支持TLS Fallback SCSV
- 是否支持压缩
- 是否有心脏滴血漏洞(heartbleed)
- 支持的密码套件(及服务器优选的preferred, 红色表示不安全算法,黄色代表中等强度的算法 )
- 证书信息
2.1 安装
(1)下载源码
[root@localname ~]# git clone https://github.com/rbsec/sslscan(2)进入目录
[root@localname~]# cd sslscan(3)编译安装
[root@localname sslscan]# make static(4)查看是否编译成功
[root@localhost sslscan]#./sslscan -version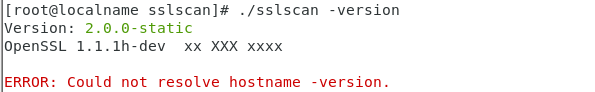
2.2 使用
[root@localhost sslscan]# ./sslscan –tlsall www.baidu.com:443
OR
[root@localhost sslscan]# ./sslscan –tlsall 192.168.5.200 —-假如192.168.5.200是你的服务器IP
PS:上述两个命令的前提是能够ping通。
[root@localname sslscan]# ./sslscan --tlsall www.baidu.com:443
Version: 2.0.0-static
OpenSSL 1.1.1h-dev xx XXX xxxx
Connected to 180.97.34.96
Testing SSL server www.baidu.com on port 443 using SNI name www.baidu.com
SSL/TLS Protocols:
TLSv1.0 enabled
TLSv1.1 enabled
TLSv1.2 enabled
TLSv1.3 disabled
TLS Fallback SCSV:
Server supports TLS Fallback SCSV
TLS renegotiation:
Secure session renegotiation supported
TLS Compression:
Compression disabled
Heartbleed:
TLSv1.2 not vulnerable to heartbleed
TLSv1.1 not vulnerable to heartbleed
TLSv1.0 not vulnerable to heartbleed
Supported Server Cipher(s):
Preferred TLSv1.2 128 bits ECDHE-RSA-AES128-GCM-SHA256 Curve P-256 DHE 256
Accepted TLSv1.2 128 bits ECDHE-RSA-RC4-SHA Curve P-256 DHE 256
Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-SHA Curve P-256 DHE 256
Accepted TLSv1.2 256 bits ECDHE-RSA-AES256-SHA Curve P-256 DHE 256
Accepted TLSv1.2 128 bits AES128-SHA
Accepted TLSv1.2 256 bits AES256-SHA
Accepted TLSv1.2 128 bits RC4-SHA
Preferred TLSv1.1 128 bits ECDHE-RSA-RC4-SHA Curve P-256 DHE 256
Accepted TLSv1.1 128 bits ECDHE-RSA-AES128-SHA Curve P-256 DHE 256
Accepted TLSv1.1 256 bits ECDHE-RSA-AES256-SHA Curve P-256 DHE 256
Accepted TLSv1.1 128 bits AES128-SHA
Accepted TLSv1.1 256 bits AES256-SHA
Accepted TLSv1.1 128 bits RC4-SHA
Preferred TLSv1.0 128 bits ECDHE-RSA-RC4-SHA Curve P-256 DHE 256
Accepted TLSv1.0 128 bits ECDHE-RSA-AES128-SHA Curve P-256 DHE 256
Accepted TLSv1.0 256 bits ECDHE-RSA-AES256-SHA Curve P-256 DHE 256
Accepted TLSv1.0 128 bits AES128-SHA
Accepted TLSv1.0 256 bits AES256-SHA
Accepted TLSv1.0 128 bits RC4-SHA
Server Key Exchange Group(s):
TLSv1.2 128 bits secp256r1 (NIST P-256)
Server Signature Algorithm(s):
TLSv1.2 Server accepts all signature algorithms.
SSL Certificate:
Signature Algorithm: sha256WithRSAEncryption
RSA Key Strength: 2048
Subject: baidu.com
Altnames: DNS:baidu.com, DNS:baifubao.com, DNS:www.baidu.cn, DNS:www.baidu.com.cn, DNS:mct.y.nuomi.com, DNS:apollo.auto, DNS:dwz.cn, DNS:*.baidu.com, DNS:*.baifubao.com, DNS:*.baidustatic.com, DNS:*.bdstatic.com, DNS:*.bdimg.com, DNS:*.hao123.com, DNS:*.nuomi.com, DNS:*.chuanke.com, DNS:*.trustgo.com, DNS:*.bce.baidu.com, DNS:*.eyun.baidu.com, DNS:*.map.baidu.com, DNS:*.mbd.baidu.com, DNS:*.fanyi.baidu.com, DNS:*.baidubce.com, DNS:*.mipcdn.com, DNS:*.news.baidu.com, DNS:*.baidupcs.com, DNS:*.aipage.com, DNS:*.aipage.cn, DNS:*.bcehost.com, DNS:*.safe.baidu.com, DNS:*.im.baidu.com, DNS:*.baiducontent.com, DNS:*.dlnel.com, DNS:*.dlnel.org, DNS:*.dueros.baidu.com, DNS:*.su.baidu.com, DNS:*.91.com, DNS:*.hao123.baidu.com, DNS:*.apollo.auto, DNS:*.xueshu.baidu.com, DNS:*.bj.baidubce.com, DNS:*.gz.baidubce.com, DNS:*.smartapps.cn, DNS:*.bdtjrcv.com, DNS:*.hao222.com, DNS:*.haokan.com, DNS:*.pae.baidu.com, DNS:*.vd.bdstatic.com, DNS:click.hm.baidu.com, DNS:log.hm.baidu.com, DNS:cm.pos.baidu.com, DNS:wn.pos.baidu.com, DNS:update.pan.baidu.com
Issuer: GlobalSign Organization Validation CA - SHA256 - G2
Not valid before: Apr 2 07:04:58 2020 GMT
Not valid after: Jul 26 05:31:02 2021 GMT2.3 sslscan原理
① sslscan通过创建多个https的连接来试探服务器支持的加密方式;
② 当使用https连接到服务器的时候,会交换双方所支持的加密方式,之后选择双发都能支持的方式进行通信;
如果https服务器配置不当,就会存在MITM攻击,攻击者就可以通过客户端支持的弱加密算法来欺骗服务器;
假如使用的是SSLV2的56位DES,当攻击者拦截并使用了这种加密流量过后,可能在很短时间之内就能够破解加密密钥。
2.4 功能
① sslscan能够检测heartbleed,这是一个openssl的漏洞;
heartbleed漏洞存在于OpenSSL TSL中,它由一个缓冲区导致,允许从内存中读取数据;实际上,Heartbleed 可以在任何未装补丁的支持 TLS 的 OpenSSL (1.0.1 到 1.0.1f 之间)服务器上利用;它从服务器内存中读取 64 KB 的纯文本数据,这能够重复执行,服务器上不会留下任何踪迹或日志。 这意味着攻击者可以从服务器读取纯文本信息,包括服务器的的私钥或者加密方式,会话 Cookie 或 HTTPS 请求会包含用户的密码或其它敏感信息。
3 nmap
https://jumpnowtek.com/security/Using-nmap-to-check-certs-and-supported-algos.html
查看证书
支持的密码套件
检测漏洞:心脏滴血 Poodle drown 等漏洞
3.1 安装
yum install nmap #输入y安装3.2 使用
(1)查看证书nmap –script ssl-cert -p 443 baidu.com
[root@localname ~]# nmap --script ssl-cert -p 443 baidu.com
Starting Nmap 6.40 ( http://nmap.org ) at 2020-08-20 16:22 CST
Nmap scan report for baidu.com (39.156.69.79)
Host is up (0.0085s latency).
Other addresses for baidu.com (not scanned): 220.181.38.148
PORT STATE SERVICE
443/tcp open https
| ssl-cert: Subject: commonName=www.baidu.cn/organizationName=BeiJing Baidu Netcom Science Technology Co., Ltd/stateOrProvinceName=Beijing/countryName=CN
| Issuer: commonName=DigiCert SHA2 Secure Server CA/organizationName=DigiCert Inc/countryName=US
| Public Key type: rsa
| Public Key bits: 2048
| Not valid before: 2020-02-27T00:00:00+00:00
| Not valid after: 2021-02-26T12:00:00+00:00
| MD5: d0cf b084 759f 231b 9b22 c197 6bd5 d271
|_SHA-1: e357 f6c5 b7d3 7464 8055 89c9 3797 c98d 9d38 2497
Nmap done: 1 IP address (1 host up) scanned in 0.60 seconds
(2)查看支持的TLS密码套件nmap –script ssl-enum-ciphers -p 443 baidu.com
[root@localname ~]# nmap --script ssl-enum-ciphers -p 443 baidu.com
Starting Nmap 6.40 ( http://nmap.org ) at 2020-08-20 16:23 CST
Nmap scan report for baidu.com (220.181.38.148)
Host is up (0.0093s latency).
Other addresses for baidu.com (not scanned): 39.156.69.79
PORT STATE SERVICE
443/tcp open https
| ssl-enum-ciphers:
| SSLv3:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_RC4_128_SHA - strong
| TLS_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_RSA_WITH_RC4_128_SHA - strong
| compressors:
| NULL
| TLSv1.0:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_RC4_128_SHA - strong
| TLS_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_RSA_WITH_RC4_128_SHA - strong
| compressors:
| NULL
| TLSv1.1:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_RC4_128_SHA - strong
| TLS_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_RSA_WITH_RC4_128_SHA - strong
| compressors:
| NULL
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 - strong
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 - strong
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 - strong
| TLS_ECDHE_RSA_WITH_RC4_128_SHA - strong
| TLS_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_RSA_WITH_AES_128_CBC_SHA256 - strong
| TLS_RSA_WITH_AES_128_GCM_SHA256 - strong
| TLS_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_RSA_WITH_AES_256_CBC_SHA256 - strong
| TLS_RSA_WITH_AES_256_GCM_SHA384 - strong
| TLS_RSA_WITH_RC4_128_SHA - strong
| compressors:
| NULL
|_ least strength: strong
Nmap done: 1 IP address (1 host up) scanned in 2.23 seconds(3) More
您还可以使用Nmap脚本查找众所周知的ssl和tls漏洞
- ssl-ccs-injection:允许MITM攻击的连接设置错误(ccs-injection-vuln,ccs-injection-primer)
- ssl-cert-intaddr:内部IP地址泄漏
- ssl-date:远程服务器时间泄漏
- ssl-dh-params:使用弱Diffie-Hellman参数
- ssl-heartbleed:易受OpenSSL Heartbleed 攻击
- ssl-known-key:服务器正在使用已知的错误证书
- ssl-poodle:服务器允许易受攻击的SSLv3 CBC密码(POODLE)
- sslv2:服务器允许使用过时的SSLv2密码
- sslv2-drown:服务器允许与DROWN攻击相关的SSLv2密码
4 testssl
testssl.sh是我们首选的测试工具,它涵盖了TLS和SSL评估所需的所有测试所需工具,并定期更新。
4.1 安装
git clone https://github.com/drwetter/testssl.sh.git4.2 testssl.sh示例
有许多可以用于testssl.sh的测试选项,您应该使用的选项将在很大程度上取决于您的测试要求。以下是部分有关testssl.sh命令行选项的示例。运行./testssl.sh可以看到所有选项。详情见 https://testssl.sh/
[root@m01ly ~]# cd testssl.sh
[root@m01ly testssl.sh]# ./testssl.sh -e www.baidu.com它是在CentOS 7上运行的, 如果你遇到相同的问题, 则可以通过以下方法解决它。Fatal error: Neither “dig”, “host”, “drill” or “nslookup” is present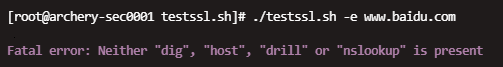
solution:当程序找不到任何实用程序来解析IP或域时, 就会发生这种情况。你可以安装bind-utils来修复错误。
yum install bind-utils -y4.2.0 测试单个主机上的TLS版本并输出到控制台
./testssl.sh -p TARGET-HOST4.2.2 测试单个主机上的所有内容并输出到HTML
./testssl.sh --warnings=batch --html 172.24.110.10:64434.2.1 测试单个主机上的所有内容并输出到控制台
./testssl.sh -e -E -f -p -y -Y -S -P -c -H -U TARGET-HOST4.2.2 测试单个主机上的所有内容并输出到HTML
./testssl.sh -e -E -f -p -y -Y -S -P -c -H -U TARGET-HOST | aha> OUTPUT-FILE.html4.2.3测试子网上的所有主机并输出到HTML
./testssl.sh -e -E -f -p -y -Y -S -P -c -H -U 192.168.1.0/24 | aha> OUTPUT-FILE.html与上述相同,但只列举每个服务器支持的密码类型:
./testssl.sh -E 192.168.1.0/24 | aha> OUTPUT-FILE.html还有很多功能。
5 SSLyze
5.1 安装
$ pip install --upgrade setuptools
$ pip install --upgrade sslyze5.2 使用
$ python -m sslyze --regular www.yahoo.com:443 www.google.com SCAN RESULTS FOR WWW.YAHOO.COM:443 - 202.165.107.50
---------------------------------------------------
* Deflate Compression:
OK - Compression disabled
* SSLV3 Cipher Suites:
Server rejected all cipher suites.
* TLSV1 Cipher Suites:
Forward Secrecy OK - Supported
RC4 OK - Not Supported
Preferred:
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA ECDH-256 bits 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
Accepted:
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH-256 bits 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA ECDH-256 bits 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_RSA_WITH_AES_256_CBC_SHA - 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA ECDH-256 bits 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA ECDH-256 bits 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_RSA_WITH_AES_128_CBC_SHA - 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
* Session Renegotiation:
Client-initiated Renegotiation: OK - Rejected
Secure Renegotiation: OK - Supported
* OpenSSL CCS Injection:
OK - Not vulnerable to OpenSSL CCS injection
* SSLV2 Cipher Suites:
Server rejected all cipher suites.
* Certificate Information:
Content
SHA1 Fingerprint: 3672d010de4097e1d06898229df2821a1b49a2a1
Common Name: *.www.yahoo.com
Issuer: DigiCert SHA2 High Assurance Server CA
Serial Number: 9093429354078714021559623999443547105
Not Before: 2020-05-11 00:00:00
Not After: 2020-11-07 12:00:00
Signature Algorithm: sha256
Public Key Algorithm: EllipticCurve
Key Size: 256
Curve: secp256r1
DNS Subject Alternative Names: [u'yahoo.com', u'*.yahoo.com', u'*.www.yahoo.com', u'mbp.yimg.com', u'*.media.yahoo.com', u'brb.yahoo.net', u'*.att.yahoo.com', u's.yimg.com', u'*.amp.yimg.com', u'fr-ca.rogers.yahoo.com', u'tw.rd.yahoo.com', u'ddl.fp.yahoo.com', u'ca.rogers.yahoo.com', u'ca.my.yahoo.com', u'add.my.yahoo.com', u'*.global.vespa.oath.cloud', u'hk.rd.yahoo.com']
Trust
Hostname Validation: OK - Certificate matches www.yahoo.com
Android CA Store (8.1.0_r9): OK - Certificate is trusted
iOS CA Store (11): OK - Certificate is trusted
Java CA Store (jre-10.0.2): OK - Certificate is trusted
macOS CA Store (High Sierra): OK - Certificate is trusted
Mozilla CA Store (2018-04-12): OK - Certificate is trusted
Windows CA Store (2018-06-30): OK - Certificate is trusted
Symantec 2018 Deprecation: OK - Not a Symantec-issued certificate
Received Chain: *.www.yahoo.com --> DigiCert SHA2 High Assurance Server CA
Verified Chain: *.www.yahoo.com --> DigiCert SHA2 High Assurance Server CA --> DigiCert High Assurance EV Root CA
Received Chain Contains Anchor: OK - Anchor certificate not sent
Received Chain Order: OK - Order is valid
Verified Chain contains SHA1: OK - No SHA1-signed certificate in the verified certificate chain
Extensions
OCSP Must-Staple: NOT SUPPORTED - Extension not found
Certificate Transparency: WARNING - Only 2 SCTs included but Google recommends 3 or more
OCSP Stapling
OCSP Response Status: successful
Validation w/ Mozilla Store: OK - Response is trusted
Responder Id: 5168FF90AF0207753CCCD9656462A212B859723B
Cert Status: good
Cert Serial Number: 06D754AE96D28371A4DEF60AC211B3E1
This Update: Aug 19 15:03:00 2020 GMT
Next Update: Aug 26 14:18:00 2020 GMT
* Resumption Support:
With Session IDs: NOT SUPPORTED (0 successful, 5 failed, 0 errors, 5 total attempts).
With TLS Tickets: OK - Supported
* TLSV1_1 Cipher Suites:
Forward Secrecy OK - Supported
RC4 OK - Not Supported
Preferred:
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA ECDH-256 bits 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
Accepted:
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH-256 bits 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA ECDH-256 bits 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_RSA_WITH_AES_256_CBC_SHA - 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA ECDH-256 bits 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA ECDH-256 bits 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_RSA_WITH_AES_128_CBC_SHA - 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
* TLSV1_3 Cipher Suites:
Server rejected all cipher suites.
* OpenSSL Heartbleed:
OK - Not vulnerable to Heartbleed
* Downgrade Attacks:
TLS_FALLBACK_SCSV: OK - Supported
* ROBOT Attack:
OK - Not vulnerable
* TLSV1_2 Cipher Suites:
Forward Secrecy OK - Supported
RC4 OK - Not Supported
Preferred:
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 ECDH-256 bits 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
Accepted:
RSA_WITH_AES_256_CCM_8 - 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 - 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 ECDH-256 bits 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
RSA_WITH_AES_256_CCM - 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH-256 bits 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_RSA_WITH_AES_256_CBC_SHA256 - 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 ECDH-256 bits 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
ECDHE_ECDSA_WITH_AES_256_CCM - 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 ECDH-256 bits 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA ECDH-256 bits 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH-256 bits 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256 - 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
ECDHE_ECDSA_WITH_AES_256_CCM_8 - 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_RSA_WITH_AES_256_CBC_SHA - 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_RSA_WITH_AES_256_GCM_SHA384 - 256 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA ECDH-256 bits 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
RSA_WITH_AES_128_CCM_8 - 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA ECDH-256 bits 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
ECDHE_ECDSA_WITH_AES_128_CCM - 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
RSA_WITH_AES_128_CCM - 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
ECDHE_ECDSA_WITH_AES_128_CCM_8 - 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 ECDH-256 bits 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_RSA_WITH_AES_128_CBC_SHA - 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_RSA_WITH_AES_128_CBC_SHA256 - 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 ECDH-256 bits 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_RSA_WITH_AES_128_GCM_SHA256 - 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 ECDH-256 bits 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 ECDH-256 bits 128 bits HTTP 302 Found - https://hk.yahoo.com/?p=us
SCAN COMPLETED IN 7.29 S6 TLSSLed
该工具是基于sslscan的脚本工具,使用非常简单。用户可以一次性执行所有检测任务,并且会生成详细的日志文件。它可以检测支持的协议类型、空密码和弱密码以及强密码等功能。
[root@localhost ~]# yum install tlssled
[root@localhost ~]# tlssled [ip/domain] 443[root@localname ~]# tlssled www.baidu.com 443
------------------------------------------------------
TLSSLed - (1.3) based on sslscan and openssl
by Raul Siles (www.taddong.com)
------------------------------------------------------
openssl version: OpenSSL 1.1.1g 21 Apr 2020
sslscan version 1.10.2
------------------------------------------------------
Date: 20200821-110138
------------------------------------------------------
[*] Analyzing SSL/TLS on www.baidu.com:443 ...
[.] Output directory: TLSSLed_1.3_www.baidu.com_443_20200821-110138 ...
[*] Checking if the target service speaks SSL/TLS...
[.] The target service www.baidu.com:443 seems to speak SSL/TLS...
[.] Using SSL/TLS protocol version:
(empty means I'm using the default openssl protocol version(s))
[*] Running sslscan on www.baidu.com:443 ...
[-] Testing for SSLv2 ...
[-] Testing for the NULL cipher ...
[-] Testing for weak ciphers (based on key length - 40 or 56 bits) ...
[+] Testing for strong ciphers (based on AES) ...
Accepted TLSv1 256 bits ECDHE-RSA-AES256-SHA
Accepted TLSv1 256 bits AES256-SHA
Accepted TLSv1 128 bits ECDHE-RSA-AES128-SHA
Accepted TLSv1 128 bits AES128-SHA
Accepted TLS11 256 bits ECDHE-RSA-AES256-SHA
Accepted TLS11 256 bits AES256-SHA
Accepted TLS11 128 bits ECDHE-RSA-AES128-SHA
Accepted TLS11 128 bits AES128-SHA
Accepted TLS12 256 bits ECDHE-RSA-AES256-SHA
Accepted TLS12 256 bits AES256-SHA
Accepted TLS12 128 bits ECDHE-RSA-AES128-GCM-SHA256
Accepted TLS12 128 bits ECDHE-RSA-AES128-SHA
Accepted TLS12 128 bits AES128-SHA
[-] Testing for MD5 signed certificate ...
[.] Testing for the certificate public key length ...
[.] Testing for the certificate subject ...
[.] Testing for the certificate CA issuer ...
[.] Testing for the certificate validity period ...
Today: Fri Aug 21 03:02:05 UTC 2020
[.] Checking preferred server ciphers ...
[*] Testing for SSL/TLS renegotiation MitM vuln. (CVE-2009-3555) ...
[+] Testing for secure renegotiation support (RFC 5746) ...
Secure Renegotiation IS supported
[*] Testing for SSL/TLS renegotiation DoS vuln. (CVE-2011-1473) ...
[.] Testing for client initiated (CI) SSL/TLS renegotiation (secure)...
(CI) SSL/TLS renegotiation IS NOT enabled (no renegotiation)
[.] Testing for client initiated (CI) SSL/TLS renegotiation (insecure)...
(CI) SSL/TLS renegotiation IS NOT enabled (no renegotiation)
[*] Testing for client authentication using digital certificates ...
SSL/TLS client certificate authentication IS NOT required
[*] Testing for TLS v1.1 and v1.2 (CVE-2011-3389 vuln. aka BEAST) ...
[-] Testing for SSLv3 and TLSv1 support ...
Accepted SSLv3 112 bits RC4-SHA
Accepted TLSv1 256 bits ECDHE-RSA-AES256-SHA
Accepted TLSv1 256 bits AES256-SHA
Accepted TLSv1 128 bits ECDHE-RSA-AES128-SHA
Accepted TLSv1 128 bits AES128-SHA
Accepted TLSv1 112 bits ECDHE-RSA-RC4-SHA
Accepted TLSv1 112 bits RC4-SHA
[+] Testing for RC4 in the prefered cipher(s) list ...
[.] Testing for TLS v1.1 support ...
TLS v1.1 IS supported
[.] Testing for TLS v1.2 support ...
TLS v1.2 IS supported
[*] Testing for HTTPS (SSL/TLS) security headers using HTTP/1.0 ...
[+] Testing for HTTP Strict-Transport-Security (HSTS) header ...
[+] Testing for cookies with the secure flag ...
[-] Testing for cookies without the secure flag ...
[*] Testing for HTTPS (SSL/TLS) security headers using HTTP/1.1 & Host ...
[+] Testing for HTTP Strict-Transport-Security (HSTS) header ...
[+] Testing for cookies with the secure flag ...
[-] Testing for cookies without the secure flag ...
[*] New files created:
[.] Output directory: TLSSLed_1.3_www.baidu.com_443_20200821-110138 ...
openssl_HEAD_1.0_www.baidu.com_443_20200821-110138.err openssl_HEAD_www.baidu.com_443_20200821-110138.log openssl_RENEG_www.baidu.com_443_20200821-110138.err
openssl_HEAD_1.0_www.baidu.com_443_20200821-110138.log openssl_RENEG_LEGACY_www.baidu.com_443_20200821-110138.err openssl_RENEG_www.baidu.com_443_20200821-110138.log
openssl_HEAD_www.baidu.com_443_20200821-110138.err openssl_RENEG_LEGACY_www.baidu.com_443_20200821-110138.log sslscan_www.baidu.com_443_20200821-110138.log
[*] done7 openssl
openssl s_client -connect www.baidu.com:443 【s_client:作为一个客户端 -connect:连接 +服务器域名:端口】 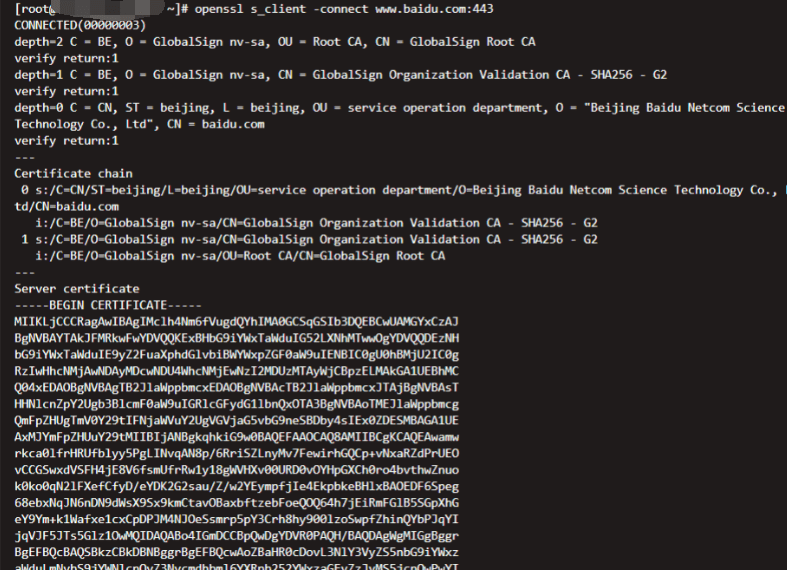
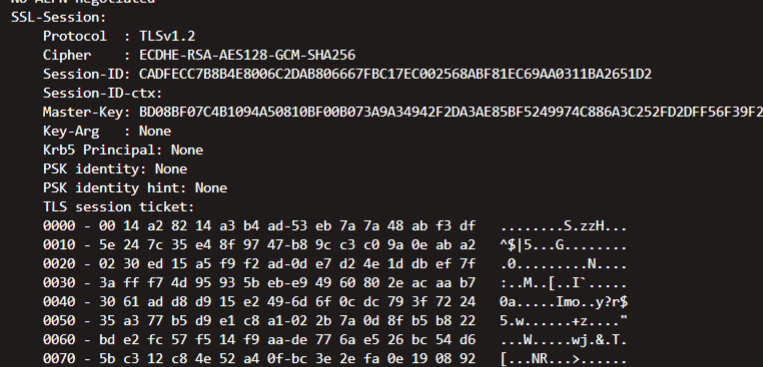
REF
https://github.com/nabla-c0d3/sslyze
https://nabla-c0d3.github.io/sslyze/documentation/
https://www.freebuf.com/sectool/99151.html